Hp Secure Key Manager User Manual Page 183
- Page / 352
- Table of contents
- TROUBLESHOOTING
- BOOKMARKS
Rated. / 5. Based on customer reviews


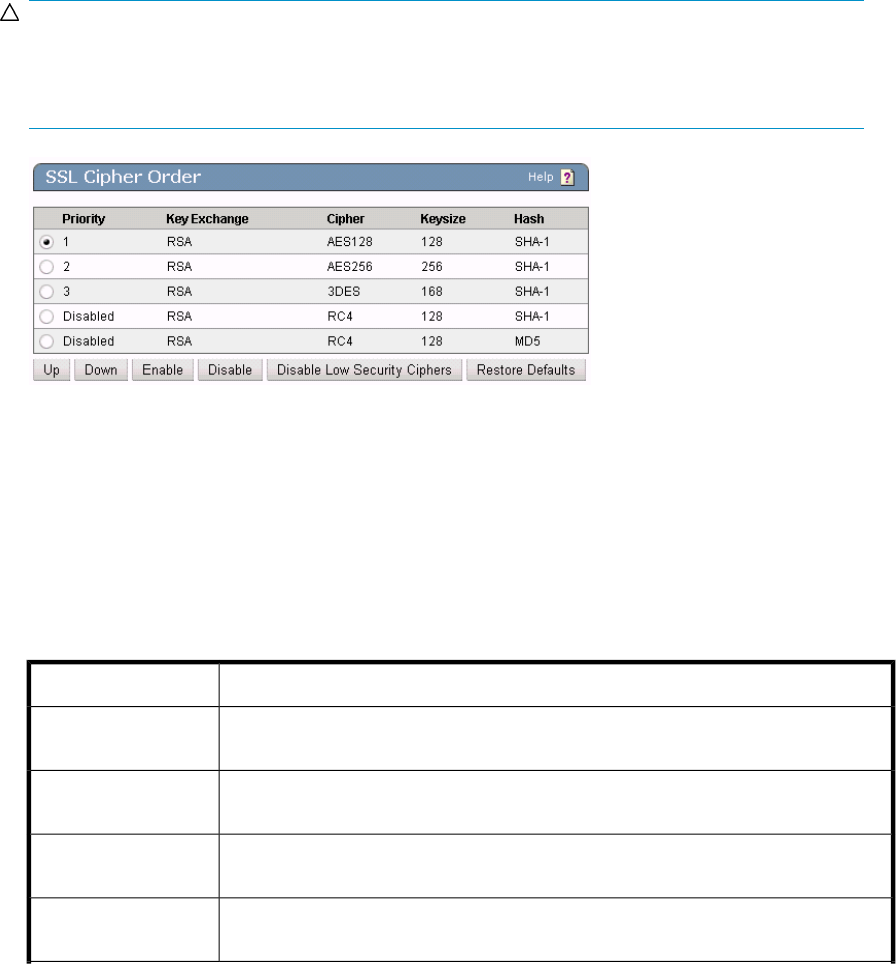
SSL Cipher Order
Use this section to enable, disable, and order the priority of SSL ciphers.
Different applications and databases support different encryption algorithms for securing SSL sessions.
The SKM supports many SSL ciphers and consequently can communicate securely using all common
ciphers.
Please note that the SSL Cipher Order pertains to the communication channel between the client
(application, database, etc.) and the SKM. It does not affect the keys that might be used to encrypt
data by the KMS Server. When an application or database presents the SKM with a list of supported
ciphers, the SKM chooses the supported cipher that is highest on its priority list.
CAUTION:
Exercise caution when modifying the SSL Cipher Order. Unless you are familiar with SSL Ciphers,
you should not rearrange the Cipher Order list. Changes to the list may affect both performance and
security. Click Restore Defaults to reset the list to the original settings.
Figure 99 Viewing the SSL Cipher Order section
The following table describes the components of the SSL Cipher Order section.
Table 80 SSL Cipher Order section components
DescriptionComponent
You can arrange the SSL Cipher order using the Up and Down buttons. One (1) is
the highest priority, and ten (10) is a low priority.
Priority
This field specifies the algorithm to use for encryption and authentication. Supported
algorithms: RSA and RSA Low Security.
Key Exchange
This field specifies the symmetric cipher to use to encrypt SSL sessions. Supported
ciphers: AES, DES, 3DES, RC2, and RC4.
Cipher
This field specifies the number of bits of the session key size. Supported key sizes
vary for each cipher.
Keysize
Secure Key Manager 183
- HP StorageWorks 1
- Secure Key Manager 1
- Contents 3
- About this guide 23
- Rack stability 24
- HP technical support 25
- Customer self repair 25
- Product warranties 25
- Subscription service 25
- HP websites 25
- Documentation feedback 26
- Tools for installation 27
- Taking ESD precautions 27
- Rack planning resources 28
- Optimum environment 29
- Temperature requirements 30
- Power requirements 30
- Unpacking 31
- Selecting a rack location 33
- Attaching the cables 35
- 2 Configuring the system 37
- Configuring the system38 38
- Configuring the system40 40
- Configuring the system42 42
- Establishing a cluster 44
- Configuring the system46 46
- Copying the certificates 48
- Installing the certificates 49
- Configuring the system50 50
- Key and policy procedures 51
- Downloading an RSA key 52
- Deleting a key 53
- User and group procedures 54
- Removing a user from a group 55
- Deleting a user 55
- Deleting a group 55
- LDAP server procedures 56
- Certificate procedures 57
- Creating a client certificate 59
- Installing a certificate 61
- Downloading a certificate 62
- Downloading a local CA 64
- Deleting a local CA 65
- Creating a local CA 65
- Installing a CA certificate 66
- FIPS status server procedures 67
- KMS server procedures 68
- Clustering procedures 70
- Setting up SSL in a cluster 71
- Date and time procedures 72
- IP authorization procedures 73
- SNMP procedures 74
- Setting up the LDAP schema 76
- Changing your password 77
- Granting credentials 78
- Revoking a credential grant 79
- Log configuration procedures 89
- Enabling syslog 90
- Enabling signed logs 90
- Log view procedures 92
- Clearing a log 93
- 4 Maintaining the SKM 95
- Backup and restore page 96
- DescriptionComponents 97
- Secure Key Manager 97 97
- Create Backup: Device Items 98
- Restore Backup 100
- Backup Restore Information 101
- Internal Backup List 101
- Services Configuration page 102
- Restart/Halt 103
- System Information page 104
- License Information 105
- Software Upgrade/Install 106
- System Health page 107
- Power Supply Status 108
- Network Diagnostics page 109
- Traceroute Information 110
- Host Information 110
- Netstat Information 110
- Reading Netstat Results 111
- Maintaining the SKM112 112
- Logging in and out 115
- Using the Home tab 115
- Security Summary 116
- System Summary 116
- Search screen 117
- Filtering sections 119
- Accessing the Help system 120
- Key Properties 123
- Versioned keys 124
- Group Permissions 125
- Custom Attributes 126
- RSA Public Key 127
- Create Query 128
- Modify Query 129
- Create Key 130
- Clone Key 132
- Import Key 132
- Authorization Policies 135
- Authorized Usage Periods 136
- Active Versions 137
- Custom Key Attributes 138
- Local Users 139
- Selected Local User 141
- Local Groups 142
- Local Group Properties 143
- User List 143
- LDAP Server Configuration 144
- LDAP Schema Properties 145
- LDAP Users 148
- LDAP Groups 148
- Certificate List 150
- Certificate Information 151
- DescriptionComponent 152
- Certificate Installation 153
- Self Signed Certificate 154
- Create Certificate Request 155
- The Default Profile 158
- CA Certificate Properties 160
- Secure Key Manager 161 161
- Sign Certificate Request 162
- Signed Certificates 162
- Create Local CA 164
- Secure Key Manager 165 165
- CA Certificate List 166
- Install CA Certificate 167
- Local CAs 168
- Advanced Security overview 169
- FIPS Compliance 171
- High Security Settings 172
- High Security Procedures 175
- FIPS Status Server overview 176
- FIPS Status Report 177
- FIPS Status Server page 179
- SSL overview 180
- SSL Sections 181
- SSL Cipher Order 183
- Configuring the KMS Server 184
- Authentication Options 185
- KMS Server Settings 186
- User Account Lockout Settings 189
- Health Check overview 190
- Health Check sections 190
- Configuring the cluster 191
- The Cluster Key 192
- Cluster Configuration page 193
- Cluster Settings 194
- Create Cluster 195
- Join Cluster 196
- Date and Time Settings 198
- NTP Settings 199
- Configuring the network 200
- Network Interfaces sections 201
- Static Route List 204
- Hostname & DNS sections 205
- Port Speed sections 206
- IP Authorization sections 207
- Allowed Client IP Addresses 208
- Configuring SNMP 209
- SNMP overview 210
- The SNMP Configuration page 211
- SNMPv1/SNMPv2 Community List 212
- SNMP Agent Settings 212
- SNMPv3 Username List 214
- SNMP Management Station List 215
- Secure Key Manager 217 217
- Enterprise MIB overview 219
- Administrator overview 220
- High Access Administrators 222
- Default Administrator 222
- Local and LDAP Administrators 222
- Administrator passwords 222
- LDAP administrators 223
- LDAP administrative server 223
- Administrator procedures 224
- Create LDAP Administrator 225
- Password Management overview 227
- Password Management sections 229
- Multiple Credentials overview 231
- Multiple Credentials sections 234
- Credentials Granted 235
- Grant a Credential 235
- LDAP Administrator Server 238
- Viewing logs and statistics 241
- Log Configuration page 244
- Log Rotation Properties 245
- Syslog Settings 247
- Log Signing 247
- Activity Log Settings 249
- Log Viewer page 250
- Audit Log 251
- Activity Log 253
- Client Event Log 255
- Statistics page 257
- System Statistics 258
- Connection Statistics 258
- Throughput 259
- License Usage 260
- Refresh Statistics (server) 261
- KMS Statistics 261
- Shell commands 263
- Command Line Interface syntax 263
- Tab completion 264
- Command modes 265
- Scripting mode 266
- Executing scripts 267
- Installing certificates 267
- CLI commands 268
- Secure Key Manager 269 269
- Secure Key Manager 271 271
- Secure Key Manager 273 273
- Activity log commands 275
- Secure Key Manager 277 277
- Secure Key Manager 279 279
- Audit log commands 280
- Autologout commands 280
- Backup and restore commands 281
- CA certificate commands 282
- Secure Key Manager 283 283
- Secure Key Manager 285 285
- Certificate commands 286
- CRL commands 289
- Secure Key Manager 291 291
- Client event log commands 292
- Diagnostic commands 294
- FIPS commands 295
- Secure Key Manager 297 297
- Help commands 298
- History commands 298
- Log commands 299
- Secure Key Manager 301 301
- Mode commands 303
- Network commands 304
- Secure Key Manager 305 305
- Secure Key Manager 307 307
- Services commands 309
- SNMP commands 311
- Secure Key Manager 315 315
- SSL commands 316
- Statistics commands 318
- System commands 319
- System health commands 322
- System information commands 323
- System log commands 323
- D Troubleshooting 325
- Troubleshooting326 326
- FCC rating label 327
- Modification 328
- Class A equipment 328
- European Union notice 329
- Japanese notices 329
- Korean notices 330
- Taiwanese notices 330
- Laser compliance notices 331
- French laser notice 332
- German laser notice 332
- Italian laser notice 332
- Recycling notices 333
- Bulgarian notice 334
- Czech notice 334
- Danish notice 334
- Dutch notice 334
- Estonian notice 335
- Finnish notice 335
- French notice 335
- German notice 335
- Greek notice 336
- Hungarian notice 336
- Italian notice 336
- Latvian notice 336
- Lithuanian notice 337
- Polish notice 337
- Portuguese notice 337
- Romanian notice 337
- Slovak notice 338
- Spanish notice 338
- Swedish notice 338
- Turkish notice 338
- Battery replacement notices 339
- French battery notice 340
- German battery notice 340
- Italian battery notice 341
- Japanese battery notice 341
- Spanish battery notice 342
- F Specifications 343
- Glossary 345
- Glossary346 346
 (102 pages)
(102 pages)







Comments to this Manuals